Data Masking
Warning
This feature is currently in beta and may be subject to change. Before using it in production, please contact your Socotra representative.
Overview
Data masking prevents users from viewing and editing specific fields within entities based on a masking level assigned to each field. Policies, quotes, and accounts are the only entity types that currently support data masking. Policies and quotes share the same data masking configuration. Currently, only extension data fields support data masking.
Data masking prevents users from accessing specific fields within an entity, unlike data access controls, which prevent users from accessing entire entities.
By default, data masking is disabled, but users will still be prevented from accessing entities if they don’t possess the necessary permissions.
Masking Levels
Fields can be assigned one of the following masking levels, in order from least restrictive to most restrictive:
none- No maskinglevel1- Sensitive informationlevel2- Confidential information
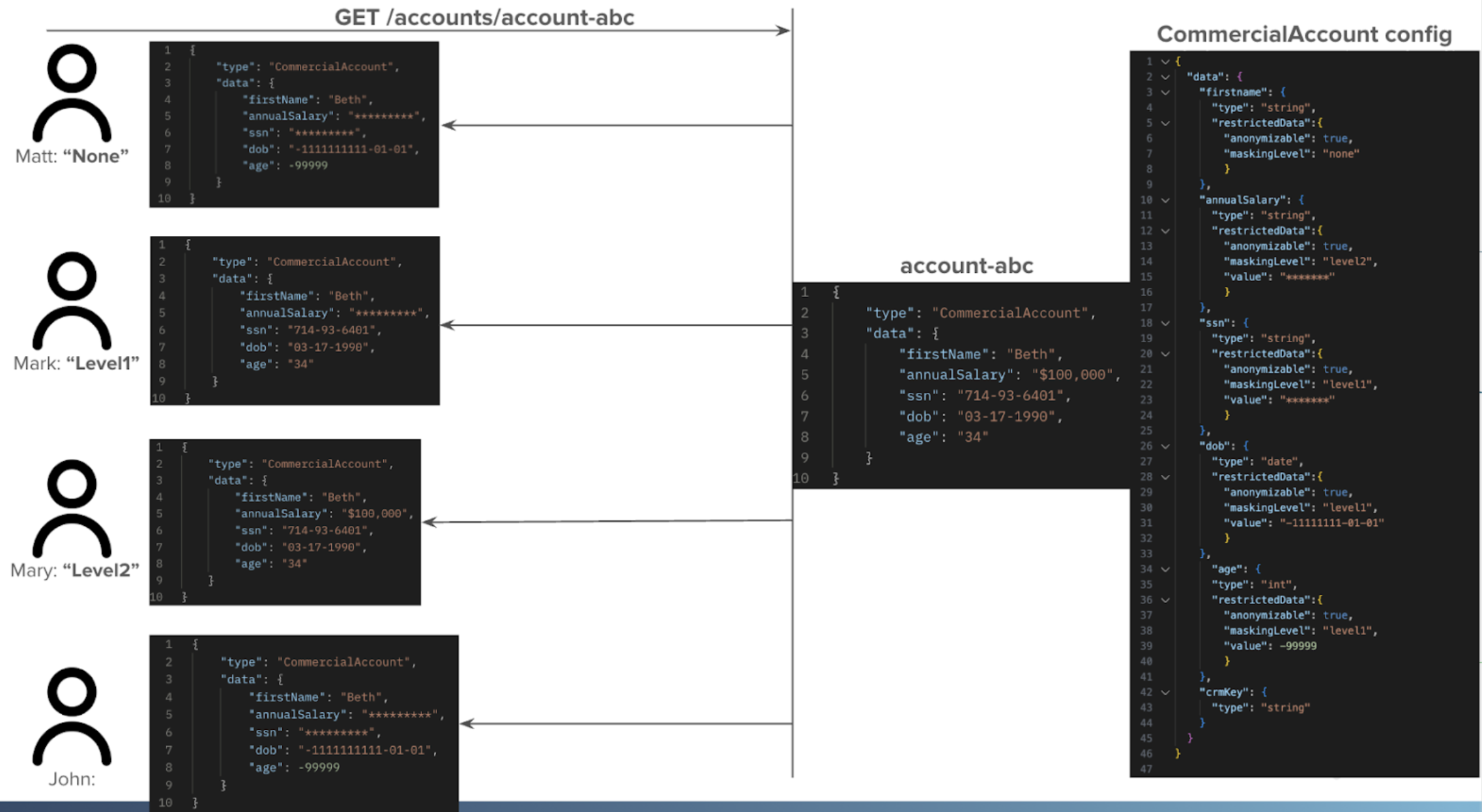
Users with a masking level of none can access fields with a masking level of none. By default, all users have a masking level of none, and all fields have a masking level of none.
Users with a masking level of level1 can access fields with a masking level of level1 and none.
Users with a masking level of level2 can access fields with a masking level of level2, level1, and none.
Enabling Data Masking
Data masking can be enabled through the DataAccessControlRef object in the tenant configuration.
requiredaccount DataAccessControlFieldRefdataMasking booleanenabled booleanpolicy DataAccessControlFieldRef
To enable data masking, set the dataMasking flag to true.
For example:
{
"dataAccessControl": {
"dataMasking": true
}
}
Assigning a Masking Level to Fields
A masking level can be assigned to each extension data field through the RestrictedDataRef object in the tenant configuration.
The maskingLevel property can be used to assign a masking level to an extension data field.
For example:
{
"data": {
"ssn": {
"type": "string",
"restrictedData": {
"maskingLevel": "level2"
}
}
}
}
Formatting Masked Values
By default, the appearance of masked values depends on the field type:
string -> *****
guid -> *****
int -> -2147483648,
long -> -9223372036854775808,
date -> -999999999-01-01T00:00:00
datetime -> -999999999-01-01T00:00:00+18:00
Masked values of the same type will always be displayed the same way, regardless of how long the value is. For instance, two different masked integers, 1 and 1000, will both be displayed as -2147483648 by default.
The value field in the RestrictedDataRef object can be used to override the default appearance of masked values. This configuration overrides the appearance of both masked values and anonymized values.
For example:
{
"data": {
"dob": {
"type": "date",
"restrictedData": {
"maskingLevel": "level2",
"value": "-11111111-01-01"
}
}
}
}
Assigning a Masking Level to Users
Users can be assigned a masking level, which allows a user to access all fields with a masking level equal to or less restrictive than the masking level assigned to the user. If a user attempts to access a field with a more restrictive masking level than the masking level assigned to the user, the user will be prevented from accessing the field and will receive a 403 Forbidden response.
The Add User Data Access API endpoint can be used to assign a masking level to a user in relation to a specific tenant. Only admins can assign a masking level to users.
The maskingLevel property in the UserDataAccessRequest can be used to specify a masking level.
requiredmaskingLevel Enum level1 | level2 | noneaccessControlFields map<string,map<string,string[]>>
For example:
{
"maskingLevel": "level2"
}
Data Masking Demonstration
Refer to the following diagram for a demonstration of data masking in action: